Sidewinder’s strategy presents users with spoofed emblems of national institutions and apparent emergency service portals. Android victims are directed to phishing websites mimicking Nepalese government services; following credential entry, the site prompts them to download an APK file masquerading as a live-update or emergency assistance app. The Windows variant relies on similarly deceptive emergency helpline portals offering downloads of executables with broad permissions, including access to file systems, cameras and microphones. These permissions are used to exfiltrate documents, images and other personal files. Analysts have observed that both malware types employ high-privilege requests after installation to maximise their data collection capability. The Windows version also establishes persistence via registry keys to ensure long-term access.
The campaign uses geopolitical tension as bait: protestors seeking updates or help during demonstrations are especially vulnerable. The lures include apps or web-interfaces styled after credible national agencies, adding a veneer of legitimacy. Security researchers note that payloads are often delivered alongside decoy content drawn from trusted media outlets, which helps to reduce suspicion and increase user engagement. The infrastructure includes malicious domains and command-and-control endpoints designed to evade detection.
Previously, Sidewinder had focused heavily on military, government and diplomatic targets across South Asia, but this wave marks a shift toward blending civic unrest with cyberattack vectors. Reports from threat-intelligence companies detail earlier Sidewinder campaigns that leveraged an old Microsoft Office vulnerability to distribute stealer malware, targeting ministries, diplomatic entities and sectors like maritime logistics. Toolsets have been refined to avoid detection, with malware dropping loader modules that sideload implants, often using signed applications to evade antivirus systems.
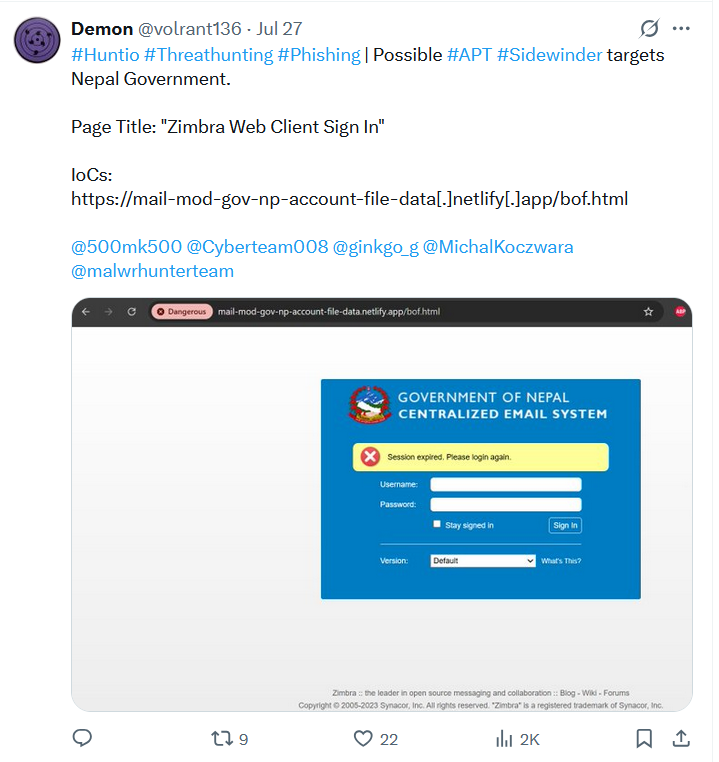
The group’s phishing infrastructure has expanded with dozens of domains impersonating government services. Many are hosted on free static site platforms such as Netlify or Pages. dev, which enable rapid deployment of deceptive pages. Common impersonated portals include webmail, secure-file systems, and file-sharing services. Central credential collection servers handle stolen credentials via POST submissions to domains under attacker control. In multiple cases these fake login pages replicate interfaces of services used by ministries of defence, law enforcement, and national webmail systems.
Experts warn that malformed emergency-style applications with high-risk permissions are particularly dangerous on Android. Once installed, these apps scan the file system for documents and images, then upload them to attacker-controlled servers. Similarly, Windows executables run background tasks harvest files with common office and image formats. In both cases, the malware is built for stealth: permissions abuse, persistence mechanisms, and mimicry of trusted entities reduce detection by non-technical users.
Topics
Technology
